Configurations
In your Google project set up Cloud Build trigger. Check cloudbuild.yaml file for more information.
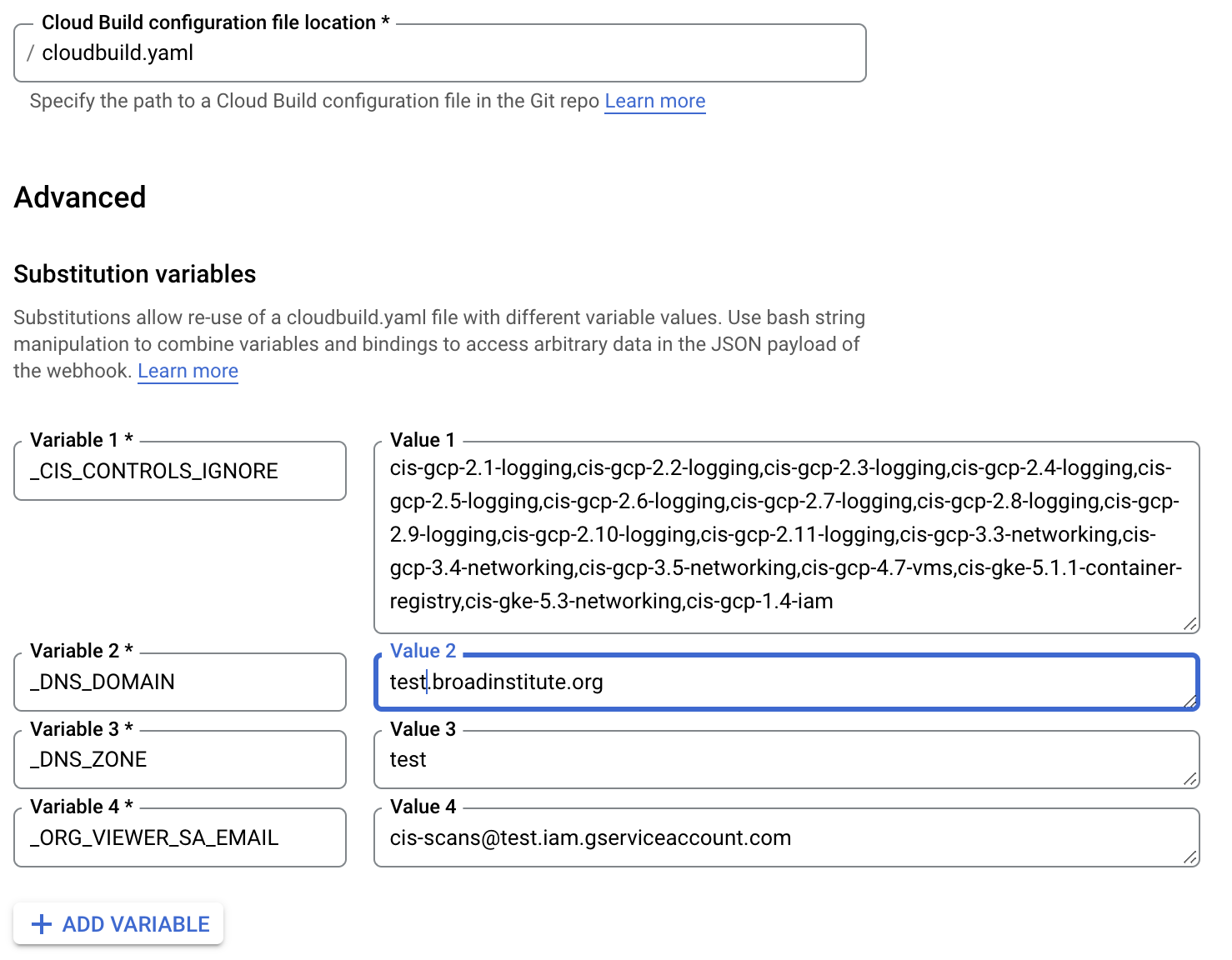
Add these to Substitution variables:
_ORG_VIEWER_SA_EMAILemail of an existing Service Account with Org Viewer role_DNS_DOMAINfully-resolved DNS domain name (e.g. appsec.example.org)_DNS_ZONEDNS zone name to be created/updated (e.g. appsec)_CIS_CONTROLS_IGNORECIS controls rule to ignore_SECURITY_CONTROLS_IGNORElist of security controls that are flagged as false positives_CODACY_ORGSin-scope Codacy organizations as a comma-delimited list_SONAR_ORGSin-scope SonarCloud organizations, as a comma-delimited list of mappings from GitHub to SonarCloud organization (e.g.githuborg=sonarcloudorg,ghorg2=scorg2)_IAP_ALLOWLISTlist of members that will have access in add/edit/delete security controls for a service endpoint,xv@companyname.com,yz@companyname.com_IAP_AUDIENCEIAP audience generated from IAP in the GCP project